FIDO stands for Fast Identity Online. FIDO2 is an extension of FIDO U2F, and offers the same level of high-security based on public key cryptography. It offers expanded authentication options including strong single factor (passwordless), strong two factor, and multi-factor authentication.
The FIDO2 authentication process eliminates the traditional threats that come with using a login username and password, replacing it with the passwordless login standard. FIDO2 is often considered a successor to the previous authentication standards, FIDO UAF and FIDO U2F.
The FIDO Alliance states that it “reflects the industry’s answer to the global password problem” by addressing legacy authentication’s challenges as they pertain to security, usability, privacy, and scalability.
Features of FIDO2:
FIDO2 Overview is shown below:
- Passwordless authentication.
- Two factor authentication.
- Multi-factor authentication.
- YubiKey 5 Series.
- Security Key Series by Yubico.
- Improved usability
- Strong account security
- One key to all accounts
- Open standard
FIDO2 Authentication options:
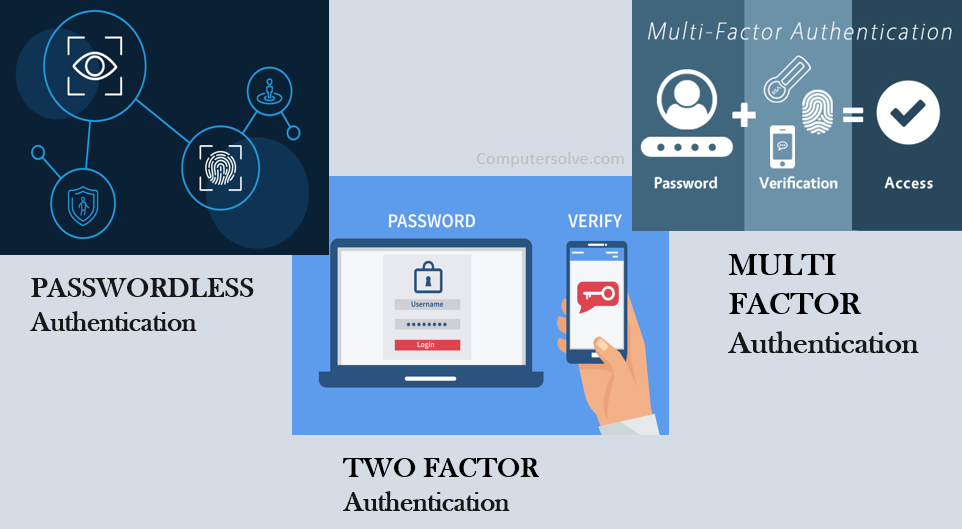
Passwordless authentication:
Strong single factor authentication using a hardware authenticator, eliminates the need for weak password-based authentication.
Two factor authentication:
Strong two factor authentication using a hardware authenticator as an extra layer of protection beyond a password.
Multi-factor authentication:
Strong multi-factor authentication using a hardware authenticator and a PIN or biometric, to meet high assurance requirements such as needed for financial transactions and ordering a prescription.
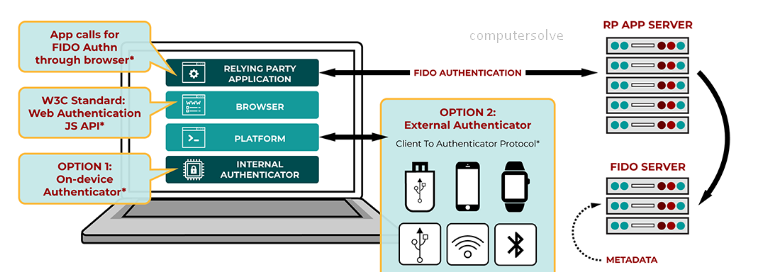
How does FIDO2 Work?
The FIDO2 standard uses a private and public key to validate each user’s identity to achieve this. The site generates a FIDO2 authentication key pair, and the user’s device sends the public key to the service. The private key is stored on the user’s device.
The following process is used when a user signs in with a FIDO2 security key:
- The user plugs the FIDO2 security key into their computer.
- Windows detects the FIDO2 security key.
- Windows sends an authentication request.
- Azure AD sends back a nonce.
- The user completes their gesture to unlock the private key stored in the FIDO2 security key’s secure enclave.
- The FIDO2 security key signs the nonce with the private key.
- The primary refresh token (PRT) token request with signed nonce is sent to Azure AD.
- Azure AD verifies the signed nonce using the FIDO2 public key.
- Azure AD returns PRT to enable access to on-premises resources.
- They provide their username and email, and the service gives them a cryptographic challenge.
You have to fill the appropriate registration form and choose a FIDO2 security key (either a FIDO2 webauthn or trusted platform module).
- The service will generate a FIDO2 authentication key pair.
- Your device sends the public key to the service, while the private key containing sensitive information stays on your device.
Once the secure communication path is enabled, the setup credentials are stored permanently, allowing for later logins. The next time you want to log in to a service, you have to follow these steps: - Provide your username and email.
- The service will give you a cryptographic challenge.
- You use your key to sign the challenge.
- The service’s server verifies your response and gives you access to your account.
FIDO2 Pros and Cons:
| PROS | CONS |
| To access your sensitive private information, attackers will need a FIDO2 key, which is physically always by your side in the form of your device. | Deal-breakers but are something you should be aware of if you plan on implementing the FIDO2 passwordless login as a security practice. |
| FIDO2 encrypts the login by default with a pair of keys (private and public) that can only be unlocked with the registered device. | Most notably, this standard requires an additional security step compared to traditional password login standards if you use it as a regular component of two-factor authentication. |
| Users unlock their cryptographic credentials with the security methods built into their devices (fingerprint sensors, facial recognition, etc.), USB keys, Bluetooth bracelets, etc. | Such a system isn’t the most practical one if you log into more FIDO2 enabled websites several times each day. Additionally, since this authentication method still isn’t well spread-out. |
| The decentralised authentication model allows high scalability. Web applications perform authentication using a standardised Javascript API supported by most modern browsers. | There are not many – FIDO2 supported sites at the moment, though the number of FIDO-enabled platforms and browsers is constantly growing. |
| Cryptographic keys are unique for each website, so they cannot be used to track the user between different sites. | This standard requires an additional security step compared to traditional password login standards if you use it as a regular component of two-factor authentication. |
Conclusion:
It has become a standard adopted by major device manufacturers and web platforms alike with ease of use, privacy, and security as its main advantages. It allows for passwordless authentication without cryptography keys being stored on a server, making it much more difficult to compromise credentials.
The FIDO Alliance has been working on standards since 2012. With this newest iteration, users can leverage their mobile devices to authenticate instead of needing a hardware key.
Using it can help improve access management. It will be even more convenient for passwordless authentication as it becomes more widely adopted.
