Computers are typically protected from viruses by the use of FIREWALLS . here in this article we will talk about computers are typically protected from viruses by the use of.
About Firewalls:
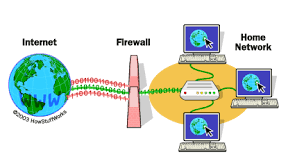
A firewall is a network security device that monitors incoming and outgoing network traffic and permits or blocks data packets based on a set of security rules. Its purpose is to establish a barrier between your internal network and incoming traffic from external sources (such as the internet) in order to block malicious traffic like viruses and hackers. if you want to disable your firewall then click on it.
A firewall is a security tool that monitors incoming and/or outgoing network traffic to detect and block malicious data packets based on predefined rules, allowing only legitimate traffic to enter your private network. Implemented as hardware, software, or both, firewalls are typically your first line of defense against malware, viruses, and attackers trying to make it into your organization’s internal networks and systems.
Software and Hardware Firewalls:
Structurally, firewalls can be software, hardware or a combination of both software and hardware.
Software Firewalls:
Firewalls can be software because software firewalls are installed separately on individual devices. They provide more granular control, in that they can allow access for one application or feature while blocking others. But they can be expensive in terms of resources since they utilize the CPU and RAM of the devices they are installed on, and administrators must configure and manage them individually for each device. Additionally, all devices within an intranet may not be compatible with a single software firewall, and several different firewalls may be required.
Hardware firewalls:
Firewalls can be Hardware because hardware firewalls, on the other hand, are physical devices, each with its own computing resources. They act as gateways between internal networks and the internet, keeping data packets and traffic requests from untrusted sources outside the private network. Physical firewalls are convenient for organizations with many devices on the same network. While they block malicious traffic well before it reaches any of the endpoints, they do not provide security against insider attacks. Therefore, a combination of both software and hardware firewalls can provide optimal security to your organization’s network.
How does a firewall work?
Firewalls protect traffic at computer entry points, called ports, where information exchange with external devices takes place. For example, “The source address 172.18.1.1 is allowed to access destination 172.18.2.1 on port 22.” Firewalls carefully analyze incoming traffic based on pre-established rules and filter traffic from unsafe or suspicious sources to prevent attacks.
Only trusted people (source addresses) are allowed to enter the house (destination addresses)—this is further filtered so that only people inside the house are allowed access to certain rooms (destination ports) , depending on whether they are the owner, a child, or a guest. The owner is allowed any number of rooms (any port), while children and guests are allowed in a certain set of rooms (specific ports).
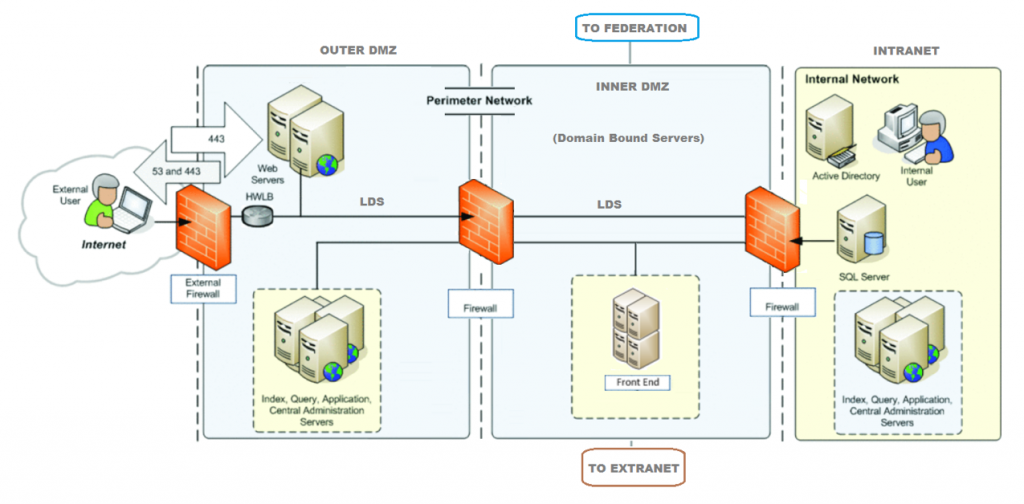
Like a metal detector door running to the main entrance to a building, a physical or hardware firewall inspects each data packet before it goes in. It checks the source and destination addresses and, based on predefined rules, determines whether the data packet should or should not pass or not. Once a data packet is inside your organization’s intranet, a software firewall can further filter traffic to allow or block access to specific ports and applications on the computer system, allowing for better control and protection from insider threats. security is allowed.
Types of firewalls:
There Are Four Types of Firewalls:
- Packet filtering firewalls.
- Stateful inspection firewalls.
- Application-level gateways (proxy firewalls)
- Circuit-level gateways.
1. Packet filtering firewalls:
Packet filtering makes firewalls very limited in their ability to protect against advanced threats and attacks. Packet filtering firewalls are the oldest, most basic type of firewall. Operating at the network layer, they simply examine the data packet against its source IP and destination IP, protocol, source port, and destination port against predefined rules to determine whether to pass the packet through. Packet filtering firewalls are essentially stateless, monitoring each packet independently without any track of established connections or packets passing through that connection.
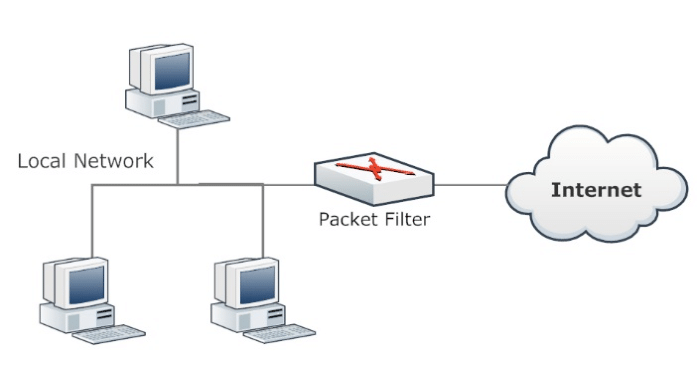
Packet filtering firewalls paved the way for modern firewalls that provide robust and deep security. Packet filtering firewalls are fast, cheap and effective. But the protection they provide is very basic. Since these firewalls cannot examine the contents of the data packets, they are unable to protect against malicious data packets coming from trusted source IPs. Being stateless, they are also vulnerable to source routing attacks and small fragment attacks.
2. Stateful inspection firewalls:
Stateful multilayer inspection (SMLI) firewalls filter packets at the network, transport, and application layers, comparing them against known trusted packets. Like NGFW firewalls, SMLI also examine the entire packet and only allow them to pass if they pass each layer individually. These firewalls examine packets to determine the state of the communication (thus the name) to ensure all initiated communication is only taking place with trusted sources.
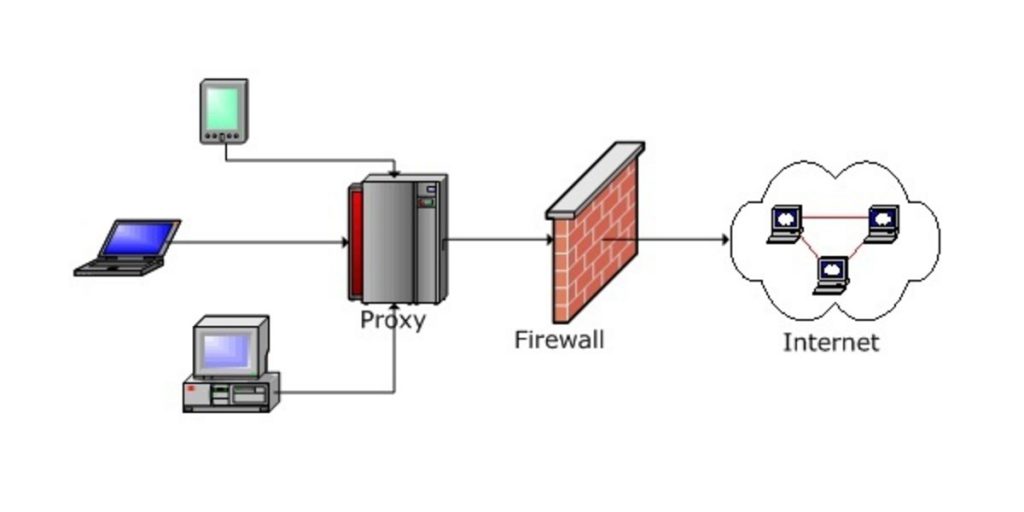
3. Proxy firewalls (Application-level gateways):
Proxy firewalls filter network traffic at the application level. Unlike basic firewalls, the proxy acts an intermediary between two end systems. The client must send a request to the firewall, where it is then evaluated against a set of security rules and then permitted or blocked. Most notably, proxy firewalls monitor traffic for layer 7 protocols such as HTTP and FTP, and use both stateful and deep packet inspection to detect malicious traffic.
4. Circuit-level gateway:
Circuit-level gateways track active sessions to established Transmission Control Protocol (TCP) connections. They are similar to packet filtering firewalls in that they perform a single check and use minimal resources. When an internal device initiates a connection with a remote host, circuit-level gateways establish a virtual connection on behalf of the internal device so that the internal user’s identity and IP address are hidden. Primarily, they determine the security of an established connection.
Their inability to inspect the contents of data packets makes them an incomplete security solution in their own right. Data packets containing malware can easily bypass circuit-level gateways if there is a valid TCP handshake. This is why another type of firewall is often configured on top of a circuit-level gateway for added security.
In this article describe that question computers are typically protected from viruses by the use of FIREWALLS so here we can expalin about firewall in computer. hope you like this article.
Thank you!!
