In this article, we will show you what is a key management server, its implementation, as well as what is the purpose of a key management server, and key features. For this you read this post completely.
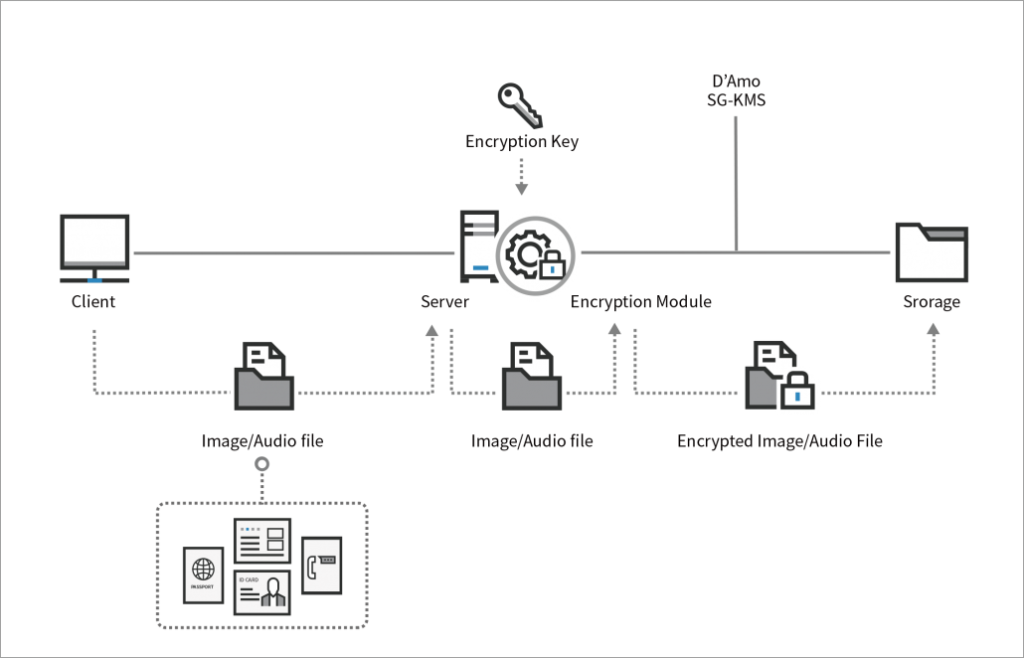
Key Management Servers (KMS) are used to operate the full lifecycle of cryptographic keys and to protect them from loss or misuse. Nowadays key management servers have become a major challenge for large government organizations and other institutions which now at a time Security cannot reach “one device”. Instead they require a cross platform, reliable data protection strategy , smartphones, drives, servers and tapes begin to be encrypted, making it harder to operate. KMS solutions, and other key management technologies, eventually control the creation, use, storage, archival, and deletion of encryption keys.
Key management server (KMS) Implementation:
Key Management Server (KMS) is used to operate the full lifecycle of cryptographic keys as well as protect them from loss or misuse. Additionally, to fully protect their loss or misuse, companies have to limit access to these keys, either by restricting physical access or controlling user access.
There is a quote from NIST about its Recommendation for Encryption Key Management and Key Management Solutions technical report that puts the KMS implementation in a slightly different context which goes something like this:
“Proper management of cryptographic keys is essential to the effective use of cryptography for security. The keys are the same as the combination of a vault. The strongest combinations known to an adversary provide any protection against safe vault penetration if that combination is secure.” Similarly, poor key management can easily compromise strong algorithms.“
Key Management Services (KMS) is a system for securely storing, managing and backing up cryptographic keys. The specific types of keys supported by each KMS differ from platform to platform. Most major management services typically allow the management of one or more of the following secrets, as described below:
- SSL certificates allow private keys
- Specifies adding SSH keys
- API keys allow
- allow code signing private keys
- Allows document signing private keys
- Database encryption keys allow
Purpose of key management server
A key management server is a third-party system in your storage environment that securely manages the authentication keys used by the self-encrypting disks in the storage system. This involves linking external key management servers to other systems that use authentication or encryption keys like your storage system does.
The storage system uses a secure SSL connection to connect to an external key management server to store and retrieve authentication keys. The communication between the storage system and the key management server uses the Key Management Interoperability Protocol (KMIP).
The key management server provides an additional level of security by storing the authentication key separately from the storage system and securely storing the authentication or encryption keys assigned to it. Additionally, authentication keys are always handled and stored securely.
key features:
These are key features of key management server:
- Support for multi-protocol, desktop, server and devices of heterogeneous environments.
- Provisioning and lifecycle management, including expiration dates and renewals.
- You create symmetric and asymmetric keys where key content can only be used to function within the service.
- Create symmetric keys where the key material is generated is used
- Import your own symmetric key material
- Defining which IAM users and roles can use keys to encrypt and decrypt data
- Temporarily disabling keys so that no one can use them
- Can schedule deletion of keys that you no longer use
